Trust center portal
Visit our Trust Center to explore our certifications, data collection practices, and compliance measures.
Security features
At NavVis, security and privacy is built into the very heart of our products and services. For the peace of mind of our customers, partners and employees, these are the safeguards we deploy as standard.
Customer files versus Instance metadata
NavVis hosts customer data in two distinct categories:
Customer files
Scanned data, either from NavVis VLX or a 3rd party laser scanner device like a TLS, and subsequent files derived from these, for example artifacts produced by customer-triggered NavVis IVION Processing tasks applied to the original scan data.
Instance metadata
Additional enrichment data produced by actions taken within NavVis IVION, such Points of Interest (POIs), measurements, user groups and permissions, etc.
Cloud hosting options for customer data
- All customer data is hosted in Amazon Web Services (AWS) data centers, in one of three available hosting locations
- Customer files are stored in AWS file storage solutions: Elastic Block Storage (EBS) and S3
- Instance metadata is stored in an AWS managed PostgreSQL database
- NavVis stores no Customer files or Instance metadata on local servers or repositories at NavVis offices without explicit customer consent
NavVis Cloud hosting architecture

Hosting options
NavVis IVION data is always stored on the Amazon AWS server location that the customer selects when creating their instance. For example: If you opt for the US region, your data will be stored on the AWS servers in the US.
The three regions are as follows:
- Europe – Germany (AWS region eu-central-1)
- North America – the United States (AWS region us-west-2)
- Asia/Pacific – Japan (AWS region ap-northeast-1)
All hosting locations are highly scalable, to support variable load from our customers, ensuring customers receive a stable and performant service globally. In addition, we use automated monitoring and alerting throughout to ensure our engineering teams are able to proactively support our customers where necessary.
Data segregation
Instance metadata is separated at the database level, with each NavVis IVION instance having its own segregated database and user in the database server within their chosen hosting region.
Customer files are stored in managed filestores hosted by AWS, with strict separation between different customers' data.
Following the principle of least privilege, each NavVis IVION instance has only access to the data storage locations required for its operation (for example, an instance without a NavVis IVION Processing subscription will not have logical access to NavVis IVION Processing storage at all). Where multi-tenant storage servers are used, strict access policies ensure that instances' storage locations are well isolated from each other.
Access management
NavVis IVION has sophisticated and granular access and user management inbuilt, empowering instance administrators to flexibly and powerfully grant or rescind access to data held within the instance.
The instance Global Admin is able to define roles across the entire instance, but can delegate authority for permission definition within specific sites to Site Admin users. This flexibility enables NavVis IVION customers to efficiently and effectively manage user access without creating a burdensome administrative bottleneck.
Each user account is listed with a “last active” timestamp, giving an “at-a-glance” overview of user activity.
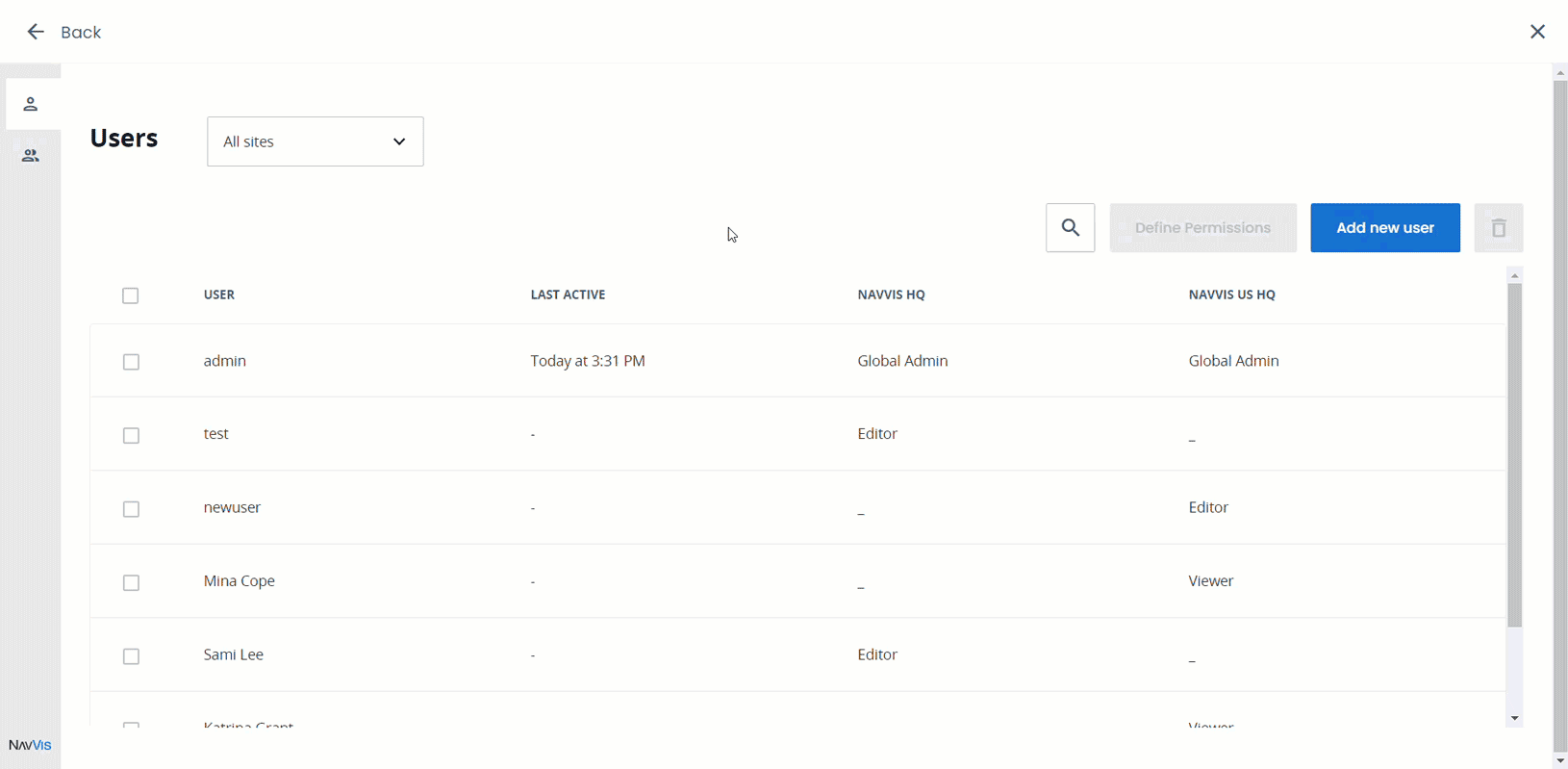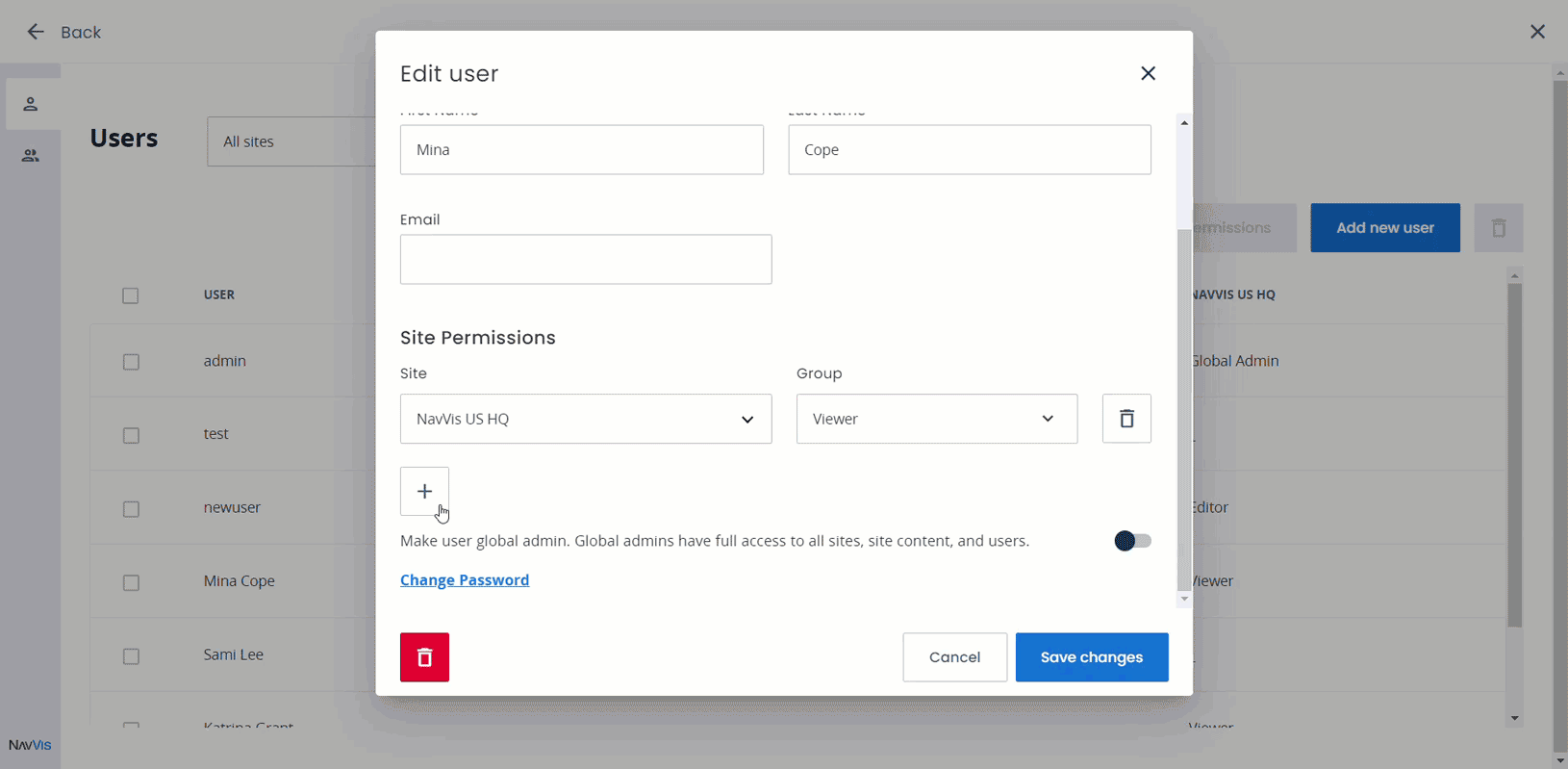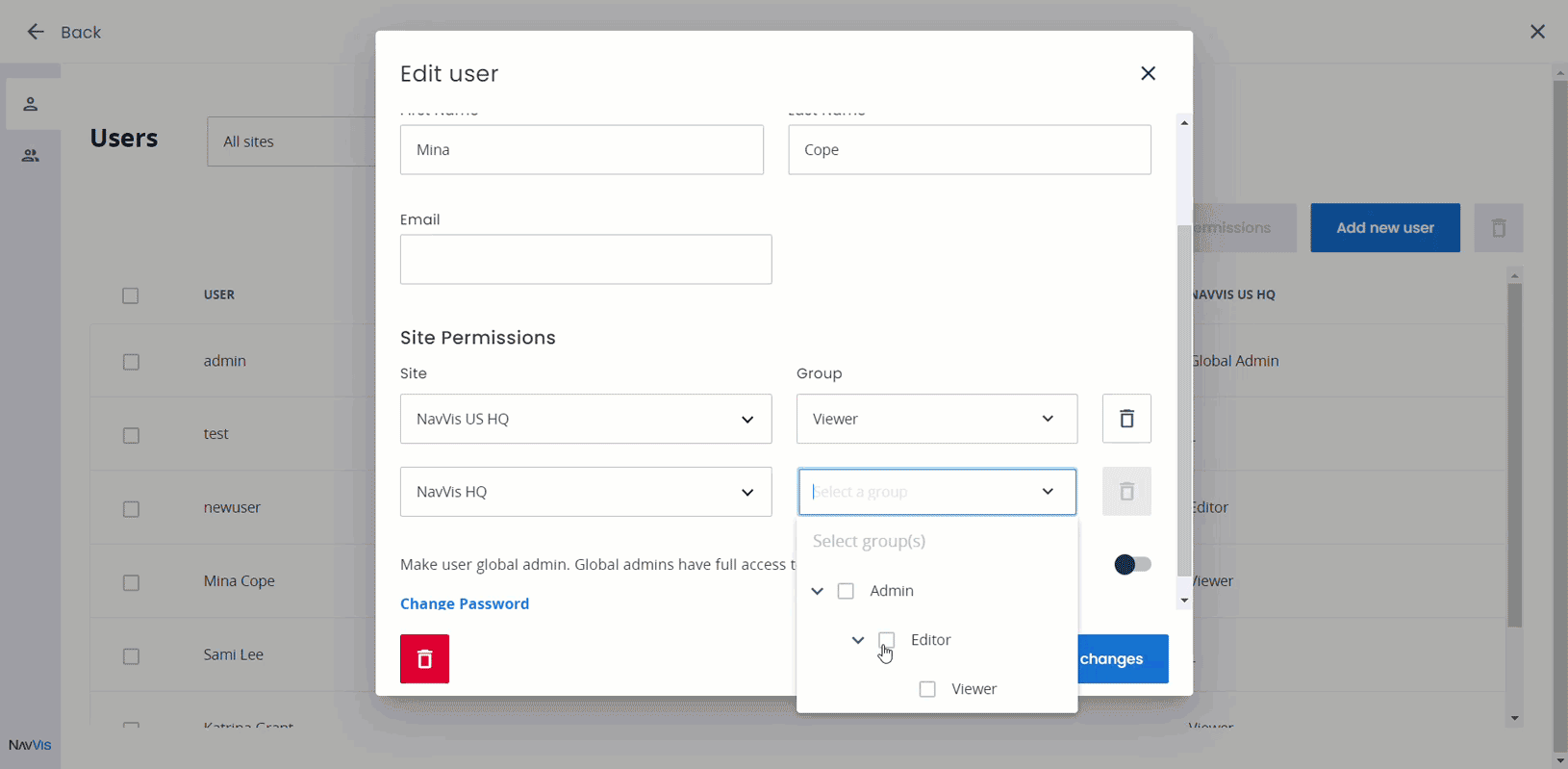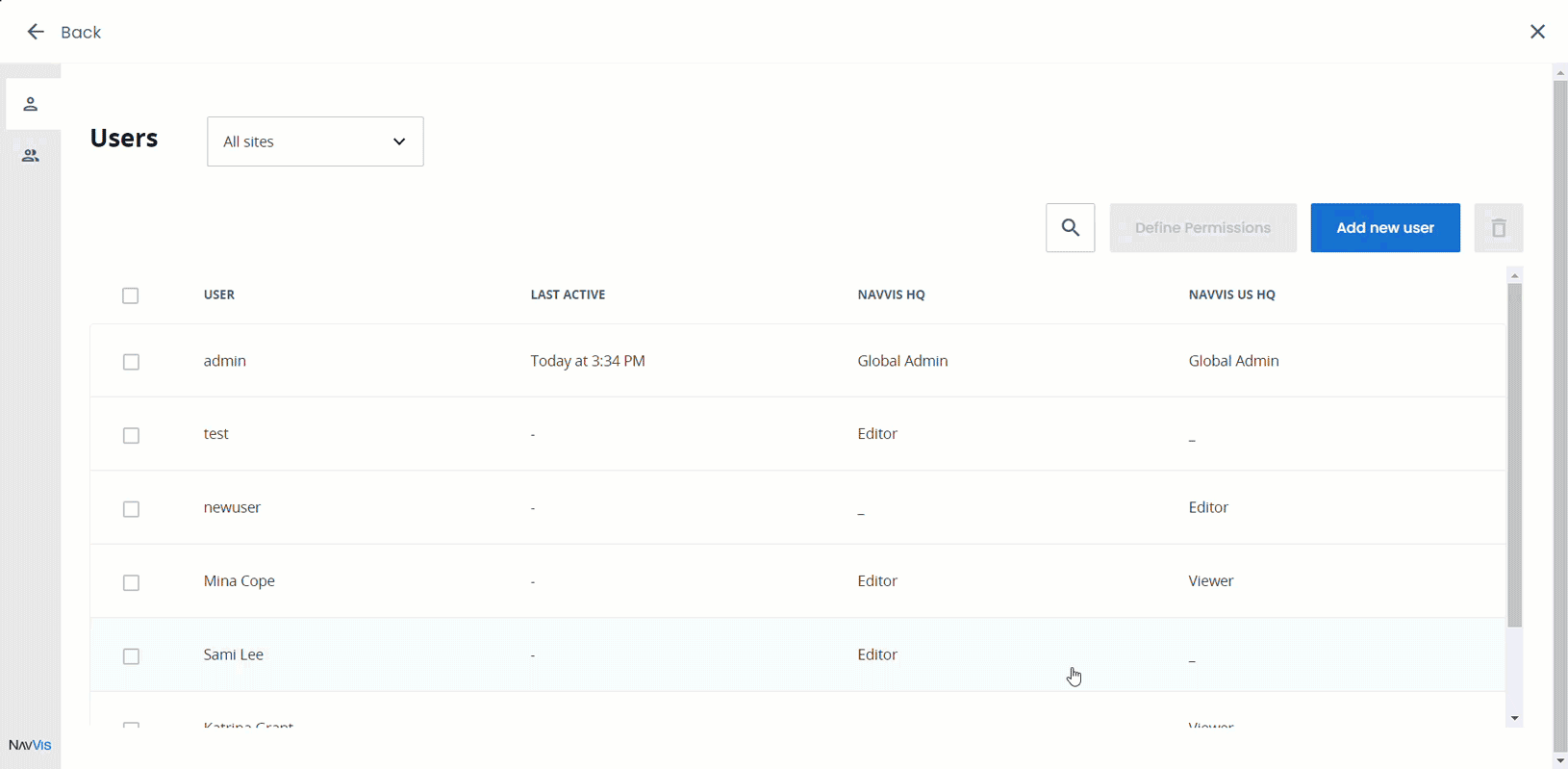
User management and permissions setting
For more information about managing users and groups in NavVis IVION see:
Authentication
NavVis IVION includes inbuilt user authentication, using a username / password pair to log in. Passwords are stored hashed and salted within the application using the BCrypt strong hashing cryptographic function, giving our customers peace of mind that their credentials are handled securely. All subscription types include this as default.
In addition to the inbuilt authentication, customers on Enterprise or Professional packages are able to take advantage of NavVis’ integration with corporate Single-Sign-On (SSO) applications. Integrating with your existing SSO solution has several advantages:
— Your users do not have to memorize another username/password combination
— Your corporate password control and user policies are applied
— User access management is simplified
NavVis IVION supports both the OpenID Connect (OIDC) and OAuth resource server protocols, enabling integration with the broadest range of standard SSO solutions.
Penetration testing
NavVis IVION undergoes four annual rounds of penetration testing by external companies. These experts look for vulnerabilities in our software and infrastructure, and attempt to find vulnerabilities we may have missed during our usual QA processes.
Issues discovered by penetration testing are reviewed, addressing any high and medium priority issues found. Low priority issues may be discussed and not addressed, with the testing company’s agreement. Full details of any resolved security issues in released versions of NavVis software is communicated via our change log.
Data retention & deletion
Once the customer’s subscription expires, the instance is taken offline and is unavailable to users. The data is retained for a short grace period of 30 days before it is deleted, during which time if the subscription is renewed it can be restored into the NavVis IVION instance when it is brought back online.
Once this period is over, the data is deleted. No copies are retained anywhere by NavVis.
Data deletion is coordinated with the customer individually, via their Account Executive at NavVis. Data will only be deleted with the explicit consent of the customer, after which no copy will be retained by NavVis.
Data is retained until the NavVis IVION instance that created it is deleted, once the applicable grace period after subscription expiry has passed. When this occurs, automated Amazon S3 lifecycle rules ensure that data held for that instance in NavVis IVION Processing is deleted within 1 day.
Data backup & disaster recovery
NavVis has taken appropriate steps to mitigate the impact of any disaster, and to minimize risk to customer data. A key aspect of this is the use of data backups, ensuring that Customer files and Instance metadata are protected. However, please note that these can only be restored by NavVis in case of disaster, not by the customer on a case-by-case-basis.
Customer files: Backups of customer files and instance metadata are taken daily and kept for 7 days. These can be restored by NavVis reverting the data to a stable point before any critical incident occurred.
Incremental backups of NavVis IVION Enterprise instances, both customer files and instance metadata are taken daily, and kept for 180 days.
Data for this service is stored in Amazon S3 storage, which offers the following guarantees:
"Designed to provide 99.999999999% durability and 99.99% availability of objects over a given year."
— Data protection in Amazon S3 - Amazon Simple Storage Service
Because of this very high level of confidence in the underlying data storage, NavVis does not make additional backups of NavVis IVION Processing data.
Business continuity management & operational resilience
Our Business Continuity Management (BCM) strategy is encapsulated by three processes: preparation, response, and recovery. Each phase plays an integral role in managing disruptions efficiently, enabling the organization to swiftly resume normal operations.
- Preparation involves pinpointing essential business functions, evaluating risks, and formulating plans to address those risks
- Response includes the immediate measures taken to manage and mitigate the effects of a disruption
- Recovery aims at strategies to quickly restore business activities to their standard operational status
Our approach to implementing BCM includes several strategic measures to strengthen our operational resilience:
- Building redundancy: we prioritize redundancy in our service design to eliminate single points of failure, ensuring continuous operation
- Periodic testing and verification: continually testing and verifying our BCM strategies is key to confirming their effectiveness in real-world scenarios
- Continuous improvement: we embrace the lessons learned from every incident and test, applying these insights to perpetually refine our processes and strategies
To support our BCM processes, we implement extensive monitoring for critical metrics within our infrastructure, with alert systems to immediately notify our team of issues. This rapid notification allows for quick response measures, reducing potential service impact.
Encryption
Encryption at rest
All data at rest is encrypted using AES 256, the industry standard for data encryption. This applies to all data in NavVis IVION and NavVis IVION Processing, regardless of sensitivity, providing a uniform layer of security across all our cloud products.
NavVis uses AWS Key Management Service (KMS) for management of the encryption keys for data at rest. This ensures our keys are kept secure, updated automatically and often, and all access and usage is audited.
Different keys are used across each of our environments (development, staging, production, etc.) to ensure isolation and security. For our NavVis IVION Enterprise separate keys are generated for each deployment, providing an additional layer of security by segregating encryption keys on a per-deployment basis.
Encryption in transit
All traffic between the client and external-facing endpoints is encrypted using Transport Layer Security (TLS) 1.2 as a minimum standard, or TLS 1.3 whenever possible. Even internal traffic that is not exposed to the public internet (such as communication between servers and other network infrastructure components) is encrypted by default, to mitigate the risk of data being intercepted within our network.
The lifecycle of TLS certificates - provisioning, renewal, and de-provisioning - is fully automated to ensure continuous protection without manual intervention.
Software development
NavVis has a Secure Development Policy covering all aspects of the software development and test lifecycle, to ensure that the software we produce continues to meet our own high standards for security. This policy, and the processes it covers, are a key part of our security certifications, and are reviewed and audited regularly.
Some key features of this Secure Development Policy are:
- All new code goes through a thorough code review process, automated tests, and manual QA
- The OWASP guidelines for secure development of web-based applications are followed at all times
- Penetration tests are carried out regularly, and any high-risk vulnerability is addressed before release
- All employee workstations, laptops, and mobile devices are managed via Microsoft’s InTune hardware management system, with antivirus installed
- Employee cloud accounts are secured using SSO, and 2FA, to minimise the risk of attacker intrusion
Compliance
To confirm our approaches meet industry best practices, NavVis undergoes regular assessments from external auditors, aligning our practices to applicable industry standards.
Find our certifications for these here, and know that we are actively expanding this list over time:

ISO 9001:2015 is a globally recognized standard for quality management, ensuring that companies have put effective processes into place to deliver impeccable products or services. NavVis is certified as of November 2023.

ISO 27001 is the international standard for information security that sets out the specification for an information security management system (ISMS). NavVis has been ISO 27001 certified since May 2021.

The Trusted Information Security Assessment Exchange (TISAX*) is a standard assessment and exchange mechanism for the automotive industry. As of April 2021, NavVis is rated TISAX assessment level 3 for information security, data protection, and connection of third parties.
*TISAX is a registered trademark and governed by ENX Association. Learn more: https://enx.com/tisax

The EU General Data Protection Regulation came into effect on May 2018, spanning all areas of data protection, accountability, and security. NavVis is aligned with GDPR rules, and our site and services are regularly reviewed for compliance.

SOC 2 is a standard developed by the American Institute of Certified Public Accountants (AICPA) that defines how companies manage and secure customer data. NavVis has been SOC 2 certified since April 2025.
SOC 2 audit report available upon request.
Report a security issue
NavVis is committed to identifying and addressing security issues that affect our software and cloud solutions. We are continuously working on improving our security processes. To report a potential security issue, please fill out the form below.
Resources






